Optimal Secure Magento Hosting
Managing the TCO (Total Cost of Ownership) of your Magento website
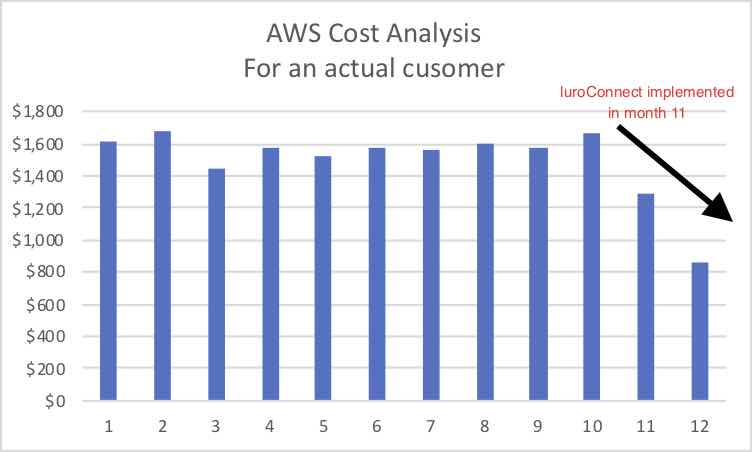
Our customers’ cloud hosting bill reduced by upto 30%. While your actual saving will vary with the state of your current hosting, we can ensure your hosting bill is optimized – you pay for what you need. Click here to know how we optimize your cloud bill.
- Optimal
- Best response times for each hit – server response is a critical factor to overall page load time.
- Planned use of memory and other resources.
- Cost effective solution – neither a cheap solution that may not work nor an over engineered expensive one that may never get used.
- Scalable
- A well defined path to scalability, depending on the business need for the next 3, 6 or 12 months or holiday period or even flash sales.
- A need to scale up as well as scale down is required.
- Secure – a security breach can be detrimental to your business, but you don’t have to spend a fortune to remain secure.
- Multi layered security for your customers’ data and the infrastructure.
- Serve valid human traffic and keep BOTs out.
- Reasonable protection against DOS attacks.
- Web Application Firewall to keep application hacks like SQL Injection at bay
- Backup and disaster recovery plan that is tested and works
Renting a server for hosting is now a commodity. Most vendors have very similar offerings. A multi vendor strategy that as far as possible avoids vendor lockin is needed. Managed hosting from a provider with multi vendor capability will help you keep your processes and choices clear.
Can this be achieved?
Hosting a Magento website does not have to be either an ignored problem nor should it be rocket science (or maybe magic even). Firm scientific principles can be used to ensure a website is well hosted and has alerts when the system goes out of capacity.
Essential Components
nginx + php-fpm
- load balance as you scale or as per traffic pattern.
- rate limit from a single IP to protect against DOS attacks.
- restrict bad IPs from accessing the sites.
- allow or keep away BOTS based on their User Agent signature.
- Secure configuration disables php execution from non code directories
- Secure hosting ensures web application cannot change code files
varnish
- Magento 2 supports varnish out-of-the-box
- Varnish is front page caching technology that stores pre-generated pages in memory and serves in milliseconds
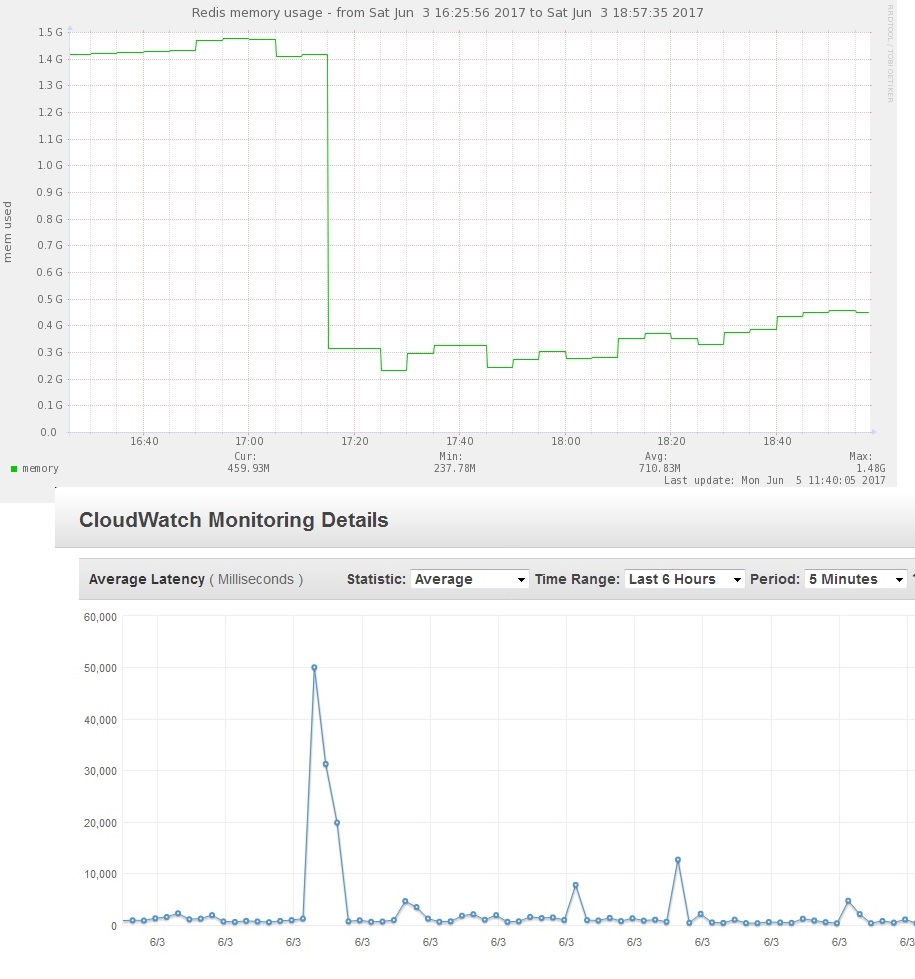
redis
- Used for storing Magento cache and sessions in memory
- sessions rejection based on rate preventing Magento lock
mysql
- oracle mysql is improving but Percona and Mariadb perform better even now
- Mysql for Magento requires configured balance between memory available and cache size.
luroConnect Insight
- Cloud tool to analyze log file data from live site
- Dashboard to show crucial parameters from the site
- Alerting when site slows or gives error
- Alerts from analyzing actual hits on the site
- See Top 10 IPs, BOTS to help decide what to block or allow
- Rate limit blocking to help find good from bad
Optional Components
Web Application Firewall (WAF)
Using Open Source ModSecurity custom built for nginx, along with custom rules for Magento we enable a reasonable level of security directly on the edge server as part of the stack. Preventing popular SQL injection and Cross Site Scripting using the OWASP ruleset (or the commercial Trustwave ruleset)
PWA hosting with vue-storefront or Magento PWA Studio
Progressive Web Apps (PWAs) are the new wave of headless eCommerce on Magento. vue-storefront is a popular option. Magento 2.3.4 ships with PWA Studio. Both require use of nodejs technology.
luroConnect supports nodejs based technology. With our advanced nginx routing rules, the application developers can decide what URLs should be served from Magento directly or from nodejs.
Secure Image Upload & Optimization
When a site needs frequent uploads of products, upload of images requires insecure access to Magento. Our solution allows safe upload to a “pod” from where images are transferred transparently and automatically to the desired folder.
Similarly our image optimization will optimize Magento generated images, either lossless or to a level of optimization acceptable, keeping the original images intact. This technology is compatible to all modern CDNs.
Also needed
- CDN